Appearance
Unlocking Software Security: A Deep Dive into Secure Code Review Best Practices 🔒🕵️♂️
"Security is not a product, but a process – let’s make it robust."
Today, we're not just discussing a concept; we're peeling back the layers of your software's foundation to reveal the critical importance of secure code review. In an era where software applications form the backbone of nearly every business, ensuring their digital integrity is no longer an option—it's a necessity. This proactive measure is your first line of defense, designed to catch vulnerabilities and bolster your application's security posture before it ever reaches the user.
A secure code review is the systematic examination of software source code with the primary goal of identifying and rectifying security flaws, weaknesses, and non-compliance issues. It's about thinking like an attacker to defend like a pro, scrutinizing every line to ensure your digital assets are resilient against the ever-evolving threat landscape.
Why is Secure Code Review Critical in the SDLC? 🚨
Integrating secure code review into your Software Development Life Cycle (SDLC) is paramount. Here's why:
- Early Vulnerability Detection: The earlier you find a bug or a vulnerability, the cheaper and easier it is to fix. Catching security flaws in the coding phase prevents costly rework, emergency patches, and potential breaches in production.
- Cost Efficiency: Remediating a security flaw in production can be exponentially more expensive than fixing it during development. Secure code review significantly reduces these long-term costs.
- Enhanced Code Quality: Beyond security, reviews enforce coding standards, improve maintainability, and reduce technical debt, leading to overall higher quality software.
- Fosters a Security-First Culture: Regular reviews educate developers on secure coding practices, instilling a security mindset that transcends individual projects. It turns every developer into a security advocate.
- Compliance and Regulatory Adherence: Many industry regulations (e.g., GDPR, HIPAA, PCI DSS) mandate rigorous security testing. Secure code review helps ensure your applications meet these critical compliance requirements.
The Secure Code Review Process: A Structured Approach 📈
Conducting a secure code review isn't a one-off task; it's a continuous, multi-stage process. A structured approach ensures thoroughness, consistency, and effectiveness.
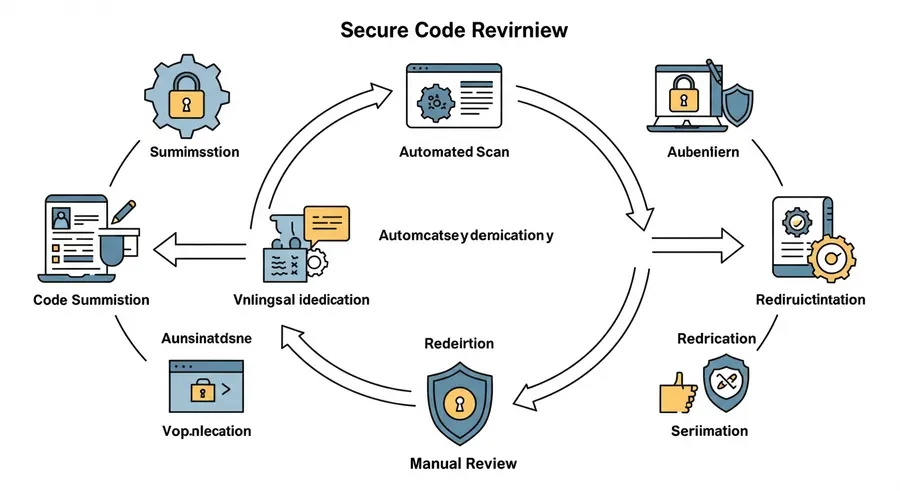
1. Defining Review Objectives 🎯
Before diving into the code, clearly define what you aim to achieve. Are you focusing on specific vulnerability types (e.g., injection flaws, authentication issues), or a general security audit? Understanding the application's architecture, its critical components, and relevant threat models will guide your review and ensure it remains focused and efficient.
2. Review Execution: Manual and Automated Scrutiny 💻
This is where the actual examination takes place. It typically involves a combination of:
- Manual Review: Human reviewers meticulously inspect code line-by-line, leveraging their expertise to spot logical flaws, business logic vulnerabilities, and contextual issues that automated tools might miss.
- Automated Review: Utilizing specialized tools to quickly scan vast amounts of code for known patterns of insecure code. This accelerates the process and handles repetitive checks.
3. Reporting and Documentation 📝
Once vulnerabilities are identified, detailed reports are crucial. These should clearly outline:
- The specific vulnerability, its location in the code, and its potential impact.
- Severity level (Critical, High, Medium, Low).
- Recommended remediation steps and best practices for fixing the issue.
- Proof-of-concept (where applicable and safe). Comprehensive documentation serves as a historical record, aiding in tracking progress and fostering continuous improvement.
4. Remediation and Follow-Up ✅
The final, vital stage. Development teams must implement the recommended fixes. After remediation, a follow-up review or re-scan is conducted to verify that the vulnerabilities have been properly addressed and no new issues have been introduced. This "trust, but verify, then verify again" approach ensures the integrity of the fixes.
Essential Tools for a Robust Secure Code Review 🛠️
To effectively conduct secure code reviews, a blend of specialized tools is indispensable.
Static Application Security Testing (SAST) Tools
SAST tools analyze source code without executing it. They act like diligent detectives, scanning for known patterns of insecure code (e.g., SQL injection, Cross-Site Scripting, buffer overflows) early in the development lifecycle.
- Pros: Catches vulnerabilities early, integrates well into CI/CD, provides immediate feedback.
- Cons: Can produce false positives, struggles with contextual or runtime vulnerabilities.
- Examples: SonarQube, Checkmarx, Snyk Code.
Dynamic Application Security Testing (DAST) Tools
DAST tools test applications in their running state by simulating attacks. They don't need access to source code and are excellent for identifying runtime errors, configuration issues, and input validation flaws.
- Pros: Detects issues in the deployed environment, identifies vulnerabilities from an attacker's perspective.
- Cons: Runs later in the SDLC, can be slower, may not cover all code paths.
- Examples: OWASP ZAP, Burp Suite.
Interactive Application Security Testing (IAST) Tools
IAST tools combine aspects of both SAST and DAST. They monitor the application during execution, providing real-time security insights by analyzing behavior and data flow from within.
- Pros: High accuracy, low false positives, provides context on vulnerabilities.
- Cons: Can be complex to set up, might impact application performance.
Software Composition Analysis (SCA) Tools
SCA tools focus on the security of third-party, open-source components, libraries, and frameworks used in your application. They identify known vulnerabilities in these dependencies by checking against public vulnerability databases.
- Pros: Crucial for supply chain security, identifies risks in widely used components.
- Cons: Relies on up-to-date vulnerability databases, can flag unused dependencies.
- Examples: OWASP Dependency-Check, Snyk Open Source, WhiteSource.
Manual Code Review 🧑💻
While automated tools are powerful, they cannot fully replace human judgment. Manual reviews are essential for uncovering logical flaws, business logic vulnerabilities, authorization issues, and complex attack paths that automated tools often miss. They also provide an opportunity for knowledge transfer and mentorship within the team.
Best Practices for Effective Secure Code Review 🛡️
To maximize the impact of your secure code review efforts, integrate these best practices:
1. Establish a Clear Secure Coding Policy 📜
Develop and disseminate a comprehensive secure coding policy that outlines standards, guidelines, and forbidden practices for all developers. This living document should cover data handling, input validation, error management, authentication, and more. Regularly update it to reflect new threats and technologies.
2. Comprehensive Training and Awareness 🧠
Invest in continuous security training for your development team. Foster a "security-first" mindset where developers understand common vulnerabilities (like the OWASP Top 10) and secure coding techniques. Hands-on exercises and workshops are highly effective.
3. Integrate Security into CI/CD Pipelines 🚀
"Shift left" your security by embedding automated SAST, DAST, and SCA scans directly into your Continuous Integration/Continuous Deployment (CI/CD) pipelines. This ensures that security checks are an integral, automated part of every build, catching issues before they even reach staging.
4. Prioritize Findings with Context 📊
Not all vulnerabilities are created equal. Prioritize findings based on severity, potential impact, and exploitability in your specific application context. Tools that offer "code-to-cloud mapping" or correlate findings with production context can help focus efforts on real risks.
5. Foster Collaborative Review Environments 🤝
Code review should be a collaborative learning experience, not a blame game. Encourage constructive feedback, knowledge sharing, and a supportive environment where developers can learn from each other's mistakes and best practices.
6. Regular Review and Iteration 🔄
The threat landscape is constantly evolving. Your secure code review practices must evolve too. Regularly review and update your policies, tools, and processes. Track metrics like defect density and mean time to remediate (MTTR) to identify bottlenecks and areas for continuous improvement.
Simple Example: Identifying a Potential SQL Injection Vulnerability 🧐
Let's look at a common vulnerability that a secure code review would flag: SQL Injection.
Consider this vulnerable Python snippet:
python
def get_user_data(username):
# DANGER: Vulnerable to SQL Injection!
query = "SELECT * FROM users WHERE username = '" + username + "';"
cursor.execute(query)
return cursor.fetchone()
# An attacker could input: username = "admin' OR '1'='1"
# The resulting query would be: SELECT * FROM users WHERE username = 'admin' OR '1'='1';
# This would bypass authentication.During a secure code review, both automated SAST tools and manual inspection would quickly identify the string concatenation used to build the SQL query as a high-risk area.
The recommended secure coding practice would be to use parameterized queries or prepared statements:
python
def get_user_data_secure(username):
# SECURE: Using a parameterized query
query = "SELECT * FROM users WHERE username = %s;" # For psycopg2 (PostgreSQL)
cursor.execute(query, (username,)) # Pass parameters separately
return cursor.fetchone()
# Or for sqlite3:
# query = "SELECT * FROM users WHERE username = ?;"
# cursor.execute(query, (username,))This simple example illustrates how secure code review guides developers towards safer programming patterns, preventing easily exploitable flaws.
Conclusion: Fortifying Your Digital Defenses 🚀
Secure code review is more than just a step in the development process; it's a fundamental pillar of modern application security. By systematically examining your source code, embracing robust tools, and committing to best practices, you empower your teams to build software that is not only functional but also inherently resilient against cyber threats.
"The only truly secure system is one that is regularly tested." Make secure code review a cornerstone of your development strategy.